-
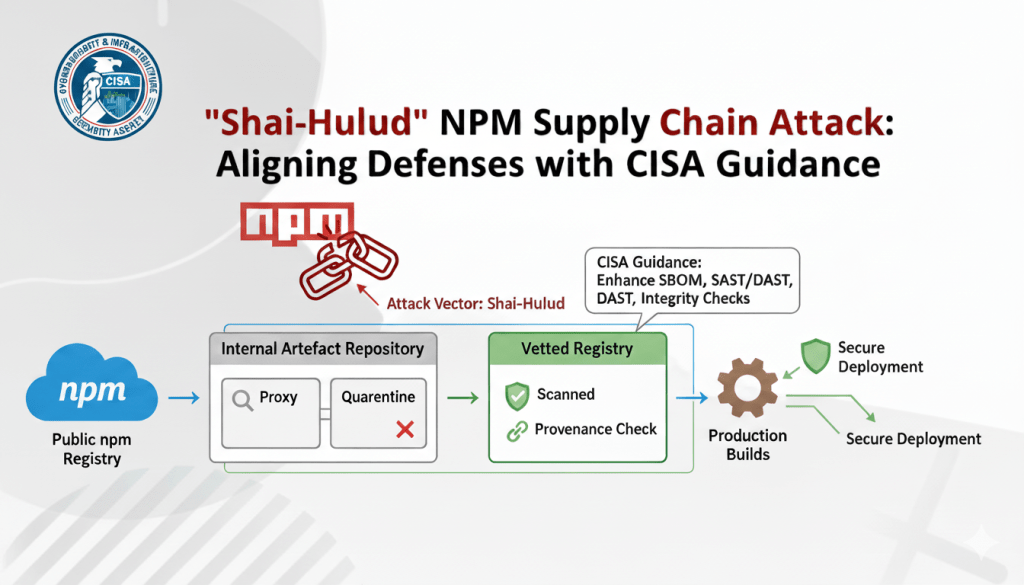
Shai-Hulud npm Worm: Aligning Supply Chain Defenses with CISA Guidance
The npm ecosystem, powering millions of JavaScript projects, has just experienced one of the most disruptive supply chain attacks to date. The Shai-Hulud worm…
-
CrowdStrike Sensor Configuration Update Incident | Impact & Remediation
KEY POINTS The recent havoc wreaked by a cybersecurity company’s update reverberated through global IT systems, causing widespread outages across various industries, including banking,…
-
Leverage Microsoft Entra Suite and Sentinel for Zero Trust Security
Microsoft has just unveiled the Microsoft Entra Suite and Microsoft Sentinel as part of the Microsoft unified security operations platform. These cutting-edge solutions aim…
- About Me (1)
- ADK (1)
- Application Version history (1)
- Azure (1)
- Azure AD Application Connector (1)
- Azure AD Application Proxy (1)
- CISA (1)
- Cloud (2)
- Cloud security (3)
- Credential Harvesting (2)
- Crowdstrike (1)
- Cybersecurity (5)
- Endpoint security & management (1)
- Github (1)
- Identity & Access (2)
- Memory dump (1)
- Microsoft (7)
- Microsoft Defender (1)
- Microsoft Defender XDR (1)
- Microsoft Entra ID Governance (1)
- Microsoft Entra Permissions Management (2)
- Microsoft Entra Verified ID (2)
- Microsoft Entra Workload ID (1)
- Microsoft Intune (8)
- Microsoft patch MS15-038 (1)
- Microsoft Security (5)
- Microsoft Sentinel (1)
- OSD (4)
- research (2)
- SCCM 2012 (7)
- SCCM Collection Query (2)
- SCCM Query Collection (1)
- Security (5)
- Software Update (2)
- Software Update scan Cycle (1)
- Strategy (2)
- Supply Chain (2)
- Task Sequence (2)
- VMWare (2)
- Windows (1)
- Windows 10 (9)
- Windows 7 (1)
- Windows 8 (1)
- Windows AutoPilot (1)
- Windows Server 2008 R2 (1)
- Windows Server 2012 R2 (1)
- Windows Update (1)